
Whenever we mention the term “hacking”, the first thing that crosses our mind is that it is illegal. But just like every coin has a flip side, the definition of hacking also has much more to it than we know! So what is hacking? Is it only for frivolous activities? Well, actually, no! There are a lot of instances when people can use hacking for good; this is what is known as white hat hacking. These people are white hat hackers.
The idea of hacking is mostly related to illegal activities, but there is much more to it than what meets the naked eye! Did you know that there are professionals who make use of white hat hacking so that they can fight cybercrime? Yes, you read it right!
Firstly, there are different kinds of hacking as well – white hat, black hat, and grey hat are the most common and well-known ones. A black hat hacker is involved in illegal hacking and directly hampers those on the receiving end. It could be hacking someone’s social media account or bank account.
Then we have got white hat hackers. As you can understand from the name itself, the major essence of a white hat hacker is that they are ethical and hence can come into a lot of use. You can choose to use white hat hackers for introspecting the black hat hackers. And finally, we have the grey hat hackers as well.
A grey hat hacker needs more knowledge of which system they are hacking into. The intent, however, might only sometimes be legal in nature.
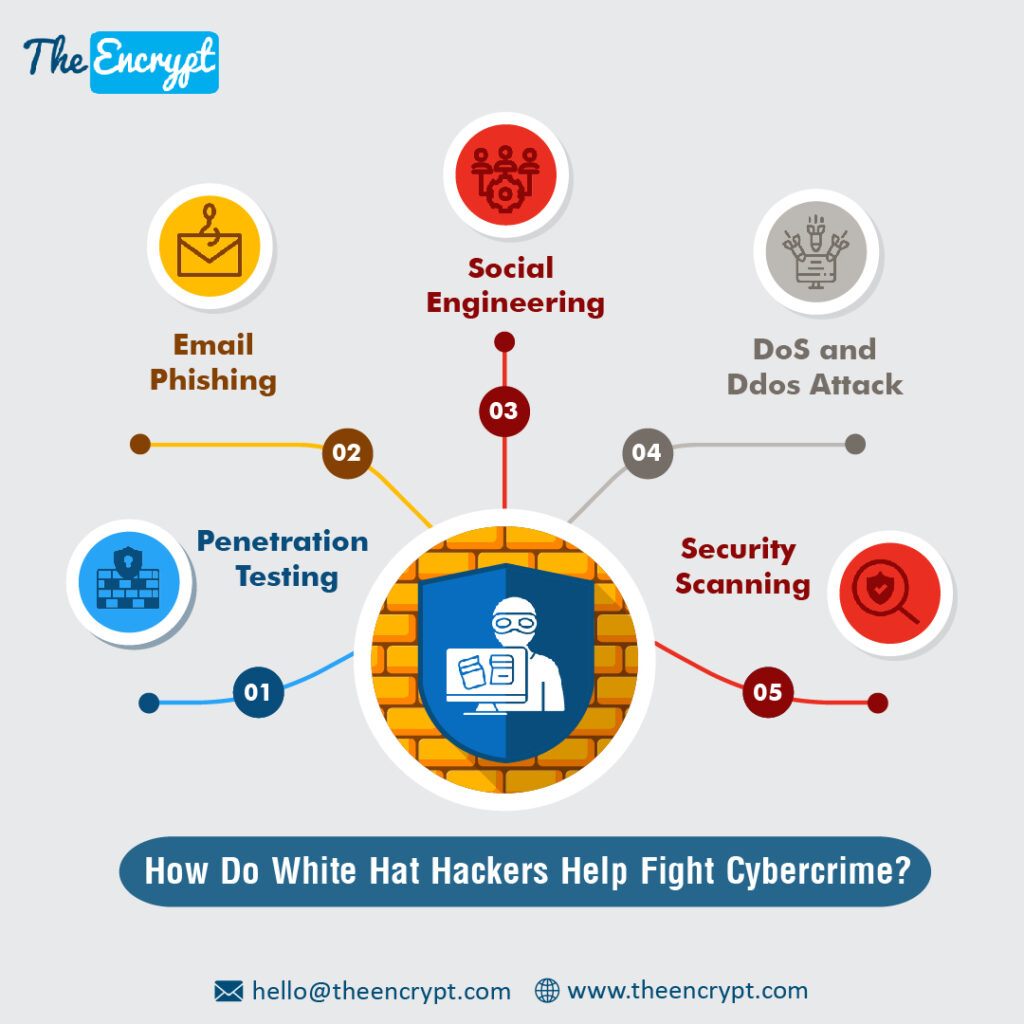
How Do White Hat Hackers Help Fight Cybercrime?
We cannot deny that the way technology is moving ahead, there is a lot more that can now be done, which we need to have information on. When we say this, it not only means positively, but sometimes there are a lot of negative effects of the same as well.
Cybercrime is an alarming field; the way it is moving forward, the day is close to becoming extremely powerful. But did you know that there are effective ways to fight cybercrime, and that too with the help of white hat hacking?
A white hat hacker is an ethical hacker, and they have the training and knowledge to stop malicious activities like cybercrime. Given the power of these white hat hackers, you will see that many government and private organisations are now introducing them to prevent such activities. But how do they help us?
Today, we will discuss the implications of white hat hacking and how it can aid one in fighting effectively with cybercrime. Some of the most common ways include:
1. Penetration Testing
The first very popular method that a lot of white hat hackers use is none other than penetration testing. So what is it?
As you can understand from the name itself, it will test how much one can penetrate through your organisation’s cyber security. So the first job of a white hat hacker is to try to hack into the organisation system and understand how difficult or easy it is to do the same. It will give one a good idea of the system’s shortcomings and strengths.
However, white hat hackers will have permission to hack through the system, which makes them different from unethical hackers.
2. Email Phishing
The next very popular method that white hat hackers use is none other than email phishing. The white hat hacker will introduce a legal phishing scam to help one know the pitfalls. The scam will be completely like a regular scam, but the only difference is that it is legal. Email phishing is a very popular method; it also helps one understand how such scams might look.
3. Social Engineering
A white hat hacker uses several techniques, and the social engineering facet is very popular among them. Cybercriminals use it to discover human responses and even tamper with it as per their requirements.
A white hat hacker will use the same technique. However, they will try to understand how human responses are shaped so that one can take effective measures. The work of a white hat hacker is to stimulate such attacks and use social engineering to understand how prone the organisation is to the attack.
4. DoS and Ddos Attack
It is a denial of service attack. What does this attack do? The major nature of this attack is that it works as a response plan for the company whenever there is an anticipated cybercrime threat.
When there is any cybercrime threat, the company does not know how to react to it, which usually causes more damage. The Dos And Ddos attack works as the immediate resource and ensures an immediate plan to fall back on when there is an anticipated attack.
5. Security Scanning
And finally, the last and very common technique that a lot of white hat hackers follow so that they can understand the weakness in the system is none other than security scanning. The nature of this form of scanning is that it tries to find out how weak the security system of your organisation is and what are the possible threats.
Security scanning is a routine process that will help one recognise all the possible threats to the open-source system.
How Does an Ethical Hacker Help?
When an ethical white hat hacker is hired in an organisation, be it private or government, there are different areas that they work in to protect from cybercrime.
One of the most important things we must remember is that any cybercrime conducted over the internet is classified as cybercrime. Hence the spectrum of crimes that the ethical white hacker has to curb potentially is also extremely widespread.
Having said that, there are specific areas that the white hat hacker generally works on to save the organisation from potential white hat hacking. Some of these are:
1. Develop Extensive Hacking Programmes for the Organization
The first thing that any white hat hacker does is try to develop an extensive hacking programme just like any other black hat hacker. The only difference is that they are authorised to do so. Why is it important?
It helps the white hat hacker understand how easy or difficult it is to hack into the organisation’s system and the potential pitfalls. This is an extremely important measure that the white hat hacker takes up, and the survey is conducted routinely.
2. Plan A Strong Internet Programme for the Organization
The next work that a white hat hacker usually has is to find out which is the strongest internet program for the organisation. It is equally important to make sure that one can build a strong system that can withstand cybercriminals’ attacks. Sometimes, these hackers must think like cybercriminals to understand which plan can affect the organisation.
3. Intervention Strategy
Once the attack has been made, what does one do? Usually, we have noticed that if a company does not have an ethical white hacker with them, they lag behind the intervention strategy. We must remember that the system is extremely weak and vulnerable after one cyber attack. This is when one needs to be active and implement the intervention strategy. A white hat hacker does it with expertise and ensures no further attacks on the system.
4. Find Out the Source of the Attack
And finally, with so many technological advancements, it is a given that there can be cyber attacks. However, a white hat hacker will be able to find the source of the attack, and based on that, the company can take up the initiative. Usually, a white hat hacker has enough aid and the ability to determine where the cyber attack was formulated. They are also known for providing damage control so the company can deal with the cyber attack better.
Are White Hat Hackers Inevitable for Stopping Cyber Crime?
It is important to understand that black and white hat hackers use similar methods to hack into a system. The only difference is that they use the hacking knowledge for extremely different end goals. Hence, until there are black hat hackers in society involved with cybercrime, hiring and encouraging white hat hackers is inevitable to deal with cybercrime.
The career scope of a white hat hacker is increasing with the passing day. They are the ultimate aids to deal better with cybercrime and curb the strength to a great extent.
Read more: What are crypto scams and how to protect yourself
